-
Products
- Discover how AVSystem keeps your business connected:
- Internet of Things
-
Communication Service Providers
- Unified Management Platform | ACS Scalable TR-069 ACS & TR-369 Controller for automated CPE management
- Broadband Service Assurance Platform Proactive access network monitoring
- DHCP Server Easy IP management for challenging networks
- Customer Experience Management Platform In-home Wi-Fi experience and access layer performance monitoring
- Fiber to the home (FTTH) Fiber to the home (FTTH) Reliable and efficient FTTH services
- Wifi Marketing
- Partner with us
- Blog
- Company
- Learn
- Careers
- Contact
- Sign in
-
Products
- Products
-
Internet of Things
-
Communication Service Providers
- Unified Management Platform | ACS Scalable TR-069 ACS & TR-369 Controller for automated CPE management
- Broadband Service Assurance Platform Proactive access network monitoring
- DHCP Server Easy IP management for challenging networks
- Customer Experience Management Platform In-home Wi-Fi experience and access layer performance monitoring
- Fiber to the home (FTTH) Fiber to the home (FTTH) Reliable and efficient FTTH services
-
Wifi Marketing
- Partner with us
- Blog
-
Company
- Company
- About us
- Clients and Partners
- News
- Learn
- Careers
- Contact
- Sign in

Unified Management Platform | ACS
TR-069 (also known as CWMP or CPE WAN Management Protocol) is an Internet protocol based on XML/SOAP. It enables remote and safe configuration of network devices.
What is TR-069 designed for?
TR-069 enables remote and safe configuration of network devices called customer premises equipment (CPE). Configuration is managed by a central server called an auto-configuration server (ACS).
- ACS Auto-Configuration Server — software that manages devices remotely. There are two AVSystem’s products that work as an ACS: UMP and Cloud ACS.
- CPE Customer Premises Equipment — any equipment used by customers which can be managed by the ACS (set-top boxes, VoIP-phones but also modems, routers, gateways, and more). CPE is commonly called a device.
How to connect a device to the ACS?
A proper connection between a device and the ACS requires few parameters to be configured on the device:
- ACS URL: an Internet address of the ACS, which is accessible from the device.
- Periodic Inform Interval: defines a frequency of communication with the ACS.
- Username and password: verification data is optional. It depends on the ACS requirements and an expected security level.
What does the communication between the device and the ACS look like?
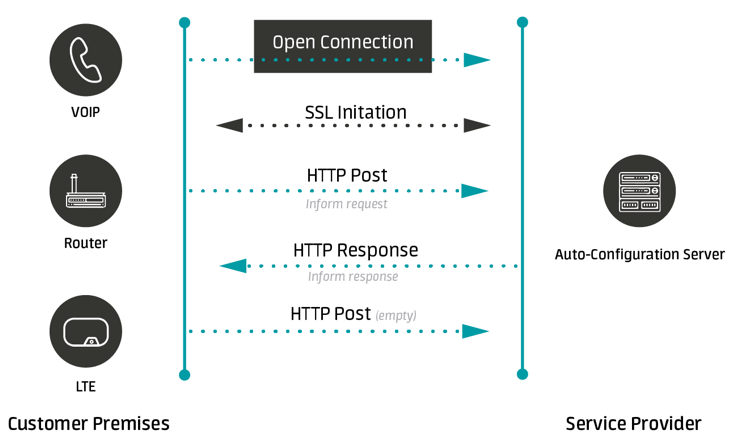
The connection between the device and the ACS is not permanent. The device establishes the connection with the ACS only at specific points in time. It usually lasts several seconds — just enough to exchange all necessary messages between CPE and the ACS. This short exchange of messages is called a provisioning session.The provisioning session is divided into a few phases:
- Session initialization:
The session is always initialized by the device that connects to the ACS. - Authentication:
The ACS must verify a username and a password provided by the device to continue the session. By default the password is not sent publicly because the HTTP Digest method is used. Additional security of the authentication can be achieved by using the HTTPS protocol with mutual certificates verification. - Device identification:
Devices are identified on the basis of information sent during initialization of the provisioning session. Namely, a device's serial number and manufacturer's unique identifier that together constitute a main identifier of the device in the ACS. A MAC address is not used as the identifier but it is saved by the ACS, making it easier to find the device in the ACS GUI later on. - Tasks execution on the device:
When the device is identified and its communication part ends, a key phase of the session starts — the ACS orders various tasks on the device. These might include reading or saving parameters, performing diagnostics, rebooting or ordering file transfers. - Session closure:
When all planned tasks have been ordered, the device closes the session. Any further tasks need initialization of a new session.
Unified Management Platform
Next-gen multiprotocol device management for telecoms
When does the device start a session with the ACS?
The device contacts the ACS in the following situations:
- The ACS URL is saved or changed on the device or the device is reset to factory settings (the device communicates it as BOOTSTRAP).
- A new periodic visit is to begin according to the value set in Periodic Inform Interval (the device communicates it as PERIODIC).
- The device responds to the ACS request for immediate connection (the device communicates it as CONNECTION REQUEST).
- A value of a parameter for which active notification is enabled changes (the device communicates it as VALUE CHANGE).
- The device is reset or is reconnected to the power supply (the device communicates it as BOOT).
- During one of the previous sessions the ACS ordered the device to initiate the contact with ScheduleInform command (the device communicates it as SCHEDULED).
- The device wants to report execution of previously ordered download or upload methods (the device communicates it as TRANSFER COMPLETE).
- The device wants to confirm a previously ordered diagnostic (the device communicates it as DIAGNOSTIC COMPLETE).
The manufacturer of the device can add custom events that will also make the device connect to the ACS. It is worth noting that the device can list a few reasons for session initialization at the same time.
Cloud ACS
Cloud-based device management via TR-069 and TR-369
Why should I be aware of reasons for session initialization?
Knowing why the device is connected to the system is useful for at least two reasons:
- You can order the device to perform various tasks depending on a particular context, for example, when the device connects for the first time.
- You can analyze reasons for last visits and find out abnormalities regarding the device’s activities.
Can the ACS initialize a session with the device?
No, it cannot. The session can be started only by the device. However, the ACS can send a request to establish connection, that is Connection Request, which makes the device contact the ACS if it is properly implemented. Connection Request is used when changes in the configuration require to be deployed immediately. Instead of waiting for the device to connect, the ACS can in advance inform the device about a need of connecting to the server, and introduce changes when it happens.
Is TR-069 secure?
Yes, it is. TR-069 provides several mechanisms that guarantee robust security
Authentication
- Device authentication uses username and password (by default HTTP Digest so the password is not sent publicly).
- SSL/TLS certificates can be used to mutually verify ACS' and device's identities.
Communication
- Device authentication uses username and password (by default HTTP Digest so the password is not sent publicly).
Other
- A proper strict configuration of the device's firewall can improve the security (a range of IP addresses that perform Connection Request should be limited to a safe pool).
What are the benefits of managing devices via TR-069?
- It offers a greater control over devices’ settings in comparison to managing them using configuration files.
- It shortens time needed for installing the devices at the customers’ premises thanks to sending the initial configuration automatically.
- It reduces a number of engineers’ visits thanks to a possibility of performing crucial operations remotely. This includes changing configuration, turning services off/on and performing diagnosis.
- It facilitates maintenance work such as upgrading a device's firmware and backing up its configuration. What is more, these long lasting operations can be scheduled to take place off-peak hours.
- It reduces failures thanks to network optimization settings for devices, for example by setting the best WiFi channels.
- It automates the control of the network state through monitoring.
- It collects data that can be used in business analysis, for example, detecting active users to whom additional offers can be made.